20210601-NEWSCTF-Nova底登陆WriteUp
WEB
easy_web
web+misc php数组key溢出,暴力破解md5 数组绕过,
得到密码
图片后面有压缩包
weblog
php 对函数和类名大小写不敏感,小写绕过,
__wakeup 那里 可以触发 __construct() 任意文件读取,读flag.php 就行
impossible ip
那个函数可以打ssrf,ssrf 本地的flag.php 可以看到源码,
然后 写入hint.txt
1 |
|
直接打就好了。
打 tcp 模式或者 unix套接字模式都可以。

至于前面那个hint , 可以 url 编码绕,挺奇怪的,我也是抱着试一下心理,用url编码绕,结果就出phpinfo() 了,很奇怪。
还有注意的点就是,不要url编码后再base64 ,我就卡在这一步一直出不来,直接将fpm流base64 编码,本来想打rce的,没成功,可能是出题人设置的吧。
weblogin
在本地搭了试了一下。
1 |
|
把序列化后的东西可见字符编码再写入data文件,编码那里出了问题,可能造成逃逸。

如果是 =xx 就不加密了,挺无聊的。
shorturl
感觉应该是非预期了
可以任意文件写入的,如果可以admin 删除 url request 然后让这些文件数量不大于1 就行。

变量覆盖导致我们可以越权成为 admin 删除文件。

这里存在反序列化漏洞,而且我们可以注入 | 来打破分隔。

在文件删除的地方可以调用,写入的时候也有调用

发一发包就好了。
Misc
very-ez-dump
扔进取证大师 拿到加密压缩包,hint提示需要找user密码。
用volatility hashdump发现是空密码。
无语子。
pslist发现有cmd进程
volatility -f ??? –profile = ??? consoles
找到了密码。
解压拿到flag。
sign in
pdf加密了。
先用pdf2john.pl 拿到hash值然后用hashcat爆破就好了,一秒出。
流量题
zip文件,打开后流量题。
搜索字符串galf找到对应的流后,提取hex编码并进行取反,脚本如下
1 | txt="????" |
保存到1.rar文件,有密码和hint。
然后用流量包的密码来解
1 | tshark -r flag1.pcapng -T fields -e urlencoded-form.value | sed '/^\s*$/d' > usbdata.txt |
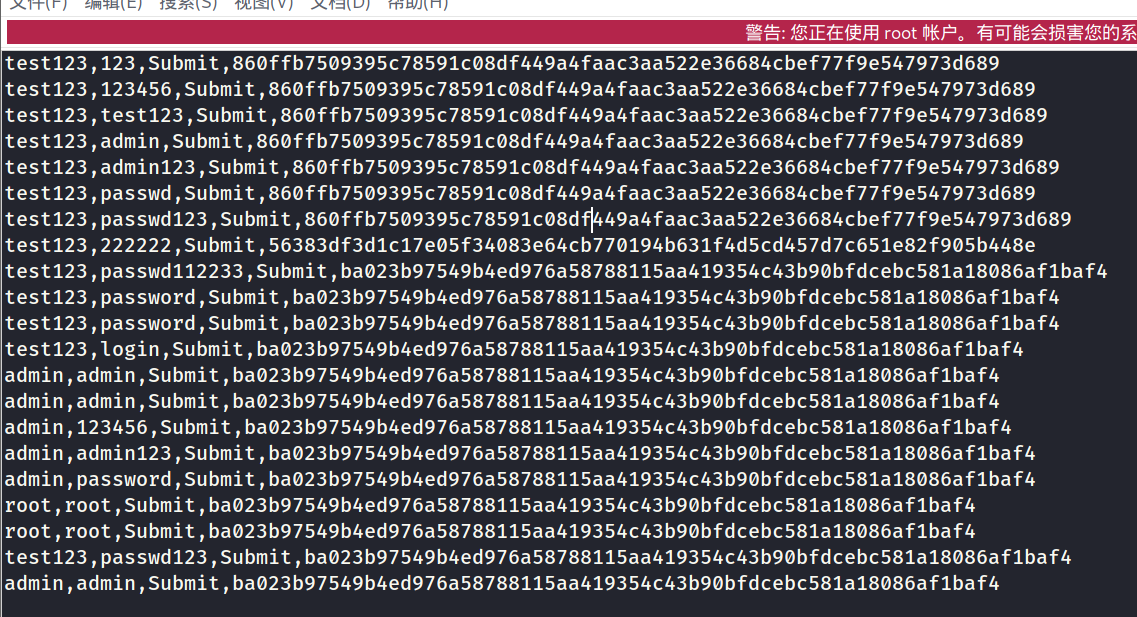
用密码一个一个试就出了。
Crypto
签到
1 | NTQ1NjcwNTg1MjMwNGU2MTRkN2E0ZTUwNTQ2YzU2NTg1NDdhNGU1NDRlMzAzNTQ3NTc0NTU5MzI0ZTQ2NTI0YjU0NTQ1NjU2NTM0NTZiMzM1MzU0MzAzZA%3D%3D |
后面多了两个url编码的东西,去掉拿去自动解密,套了几个base而已
字符串与字节
1 | 010101100100010101110101010001010100010001000101010101100100011001010110011001000100010001000110011001100110010001100100010101100100010001010101010101010101010101000110 |
第一段可以直接转字节,得到
1 | VEuEDEVFVdDFfddVDUUUF |
看了官方的WP,奇数偶数位
-2c9d444a.png)
rsa256
这个文件的日期我很好奇
-3acfd61c.png)
基础的二进制文件读取和rsa公钥提取,主要考验rsa库函数的一些运用
1 | flag{3b6d3806-4b2b-11e7-95a0-000c29d7e93d} |
贴一下脚本
1 | from gmpy2 import invert |
big exponent
题目代码
1 | from Crypto.Util.number import * |
n可以分解
1 | p = 101762447604961968347497011921099322367324119881977823223715806843654916018223203152717441386396615480134613864942068489600487206751473112264495957512819776729786840027245275219664091321087832913341367749452671938119115622233015167030327196487127307195872792552039408988207189866115101567965404039921455793363 |
1 | flag{welcome_to_2th_compettion_2021} |
Reverse
signin
主要的问题是pyc文件没有反编译成功
-0d2d4d1c.png)
然后尝试百度之后,这道题最后的解法是
查看内码,试图反编译pyc,结果看到内码发现,不对啊,就是那么短,应该是文件的问题了
-80bbc7bd.png)
好在第二天题目上了hint,直接求冒泡排序的次数,小手动一动,flag天上来
1 | #!/usr/bin/env python |
1 | synt{jrypbzr_gb_arjfpgs} |
然后凯撒一下得到
1 | flag{welcome_to_newsctf} |