20210731-DAS & 极客巅峰 & UIUCTF2021 & Cryptoctf-CryptoSecPartWriteUp
2021DASCTF实战精英夏令营暨DASCTF July X CBCTF 4th
Crypto-Yusa的密码学签到——BlockTrick
1 | from Crypto.Cipher import AES |
脑洞题,尚师傅给的思路,两轮AES_CBC,用已知IV去异或
1 | # !/usr/bin/env python |
Crypto-Yusa的密码学课堂——SEDSED
1 | import os |
My_box
1 | # 64->56 |
复现了下DES的流程
整道题的思路就是用一组随机的key去加密了已知的testtest得到结果77a35598c47aeea6,并用相同的key去加密我们的flag;那么解题的思路也很明了了,通过已知的明密文设法得到key,然后写解密函数,最终返回到
先搞key1(图中的key1我随便写的),只需要关注上面那个feistel结构
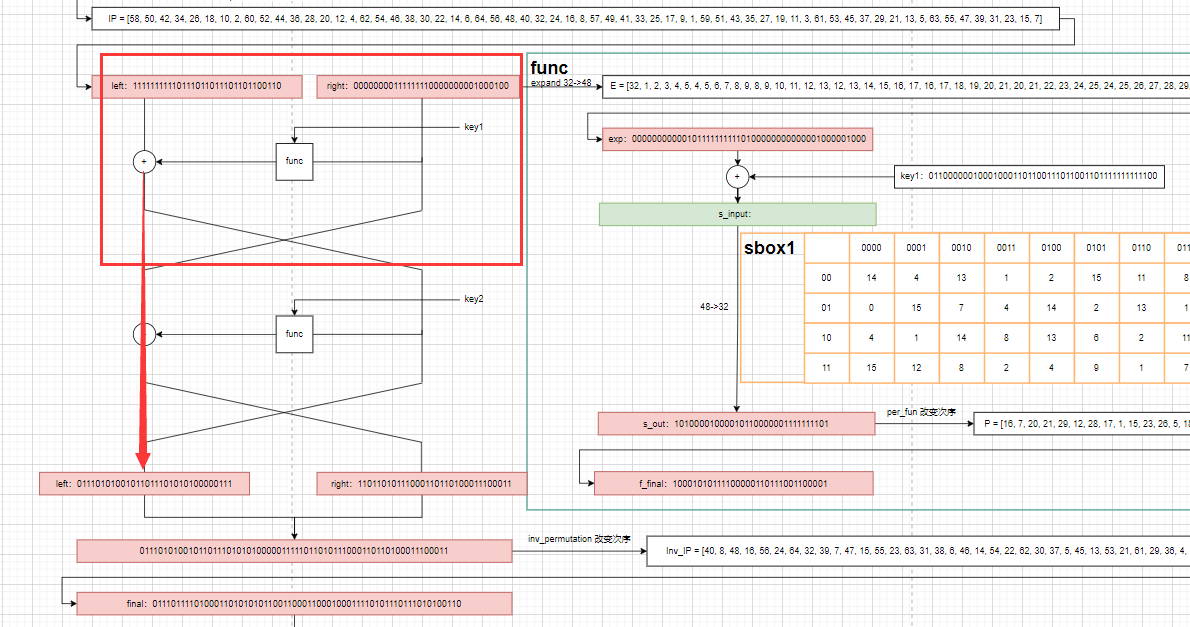
有些是可以直接逆回去的部分,形如inv_permutation和per_func这两个函数,就可以这样逆回来,写的有点臭屁
1 | def inv_permutation(text): |
1 | null = ['' for _ in range(64)] |
然后本题最为关键的就是爆破这个sbox;关于sbox的工作原理,简单来说就是将48位转成32位,中间是每6位转8位,就如wiki百科上以sbox5为例,011011首尾是01,中间是1101,也就是对应坐标1,13,对应到沙盒(这个是可以查表的)就是1001。这样一顿操作下来,就把原来总长48位的,拆分成8个小组,每组6位变成4位,从而最后的总长度为32。显然这个过程是不可逆的
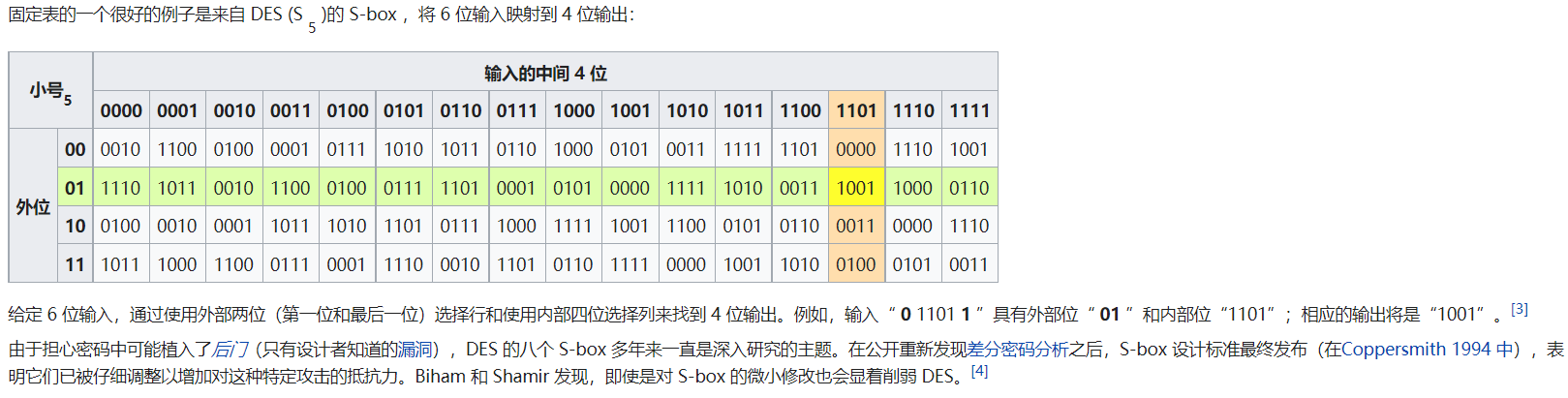
仔细观察沙盒发现一行中是0~15这16个数字打乱顺序,所以一个沙盒要爆破4种情况
写了下脚本,可能有点问题
1 | #!/usr/bin/env python |
Misc-red_vs_blue
Misc的签到题
给了一个nc,连上玩一下就知道是两种情况让你猜,连续猜对66次得flag,每次连nc输赢的结果不同
写了个脚本,但是有些交互的问题,总之还是一句话一句话接收吧
1 | #!/usr/bin/env python |
极客巅峰
Crypto-crtrsa
1 | from secret import flagn,p,q |
1 | e = 2953544268002866703872076551930953722572317122777861299293407053391808199220655289235983088986372630141821049118015752017412642148934113723174855236142887 |
e很大,但是显然d也很大;从已知看,像dp泄漏,但e太大,枚举不了;最后看到RSA - Small CRT Private Exponents
没找到代码,看不懂论文(feiwu
用RsaCtfTool中的一个工具small_crt_exp,参考https://github.com/Ganapati/RsaCtfTool,直接把脚本拿来改了下,exp如下
1 | # sage |
用这个可以分解出p
来自天命团队的密码师傅直接推导出来,从dp这个可以爆破点入手,求出了p,强。参考天命团队wp
Crypto-MedicalImage
1 | from PIL import Image |
不知道为什么没有出,找到混淆函数,然后加密和解密很类似,最后跑了6400张图片,没有解出来
1 | #!/usr/bin/env python |
看了来自天命团队的WP,还是逆算法的问题,想太简单了,以为加密即解密,稍微改一下就行
摆出re的态度,先cp下源码,自己重新写下
1 | from PIL import Image |
然后我怎么也想不到会死在这里
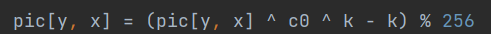
运算优先级,异或没有加括号,位运算的优先级比加减要低
顺带发现师傅只爆破了16种情况
我出来是25张flag
1 | #!/usr/bin/env python |
UIUCTF 2021
Re-hvhpgs{synt}
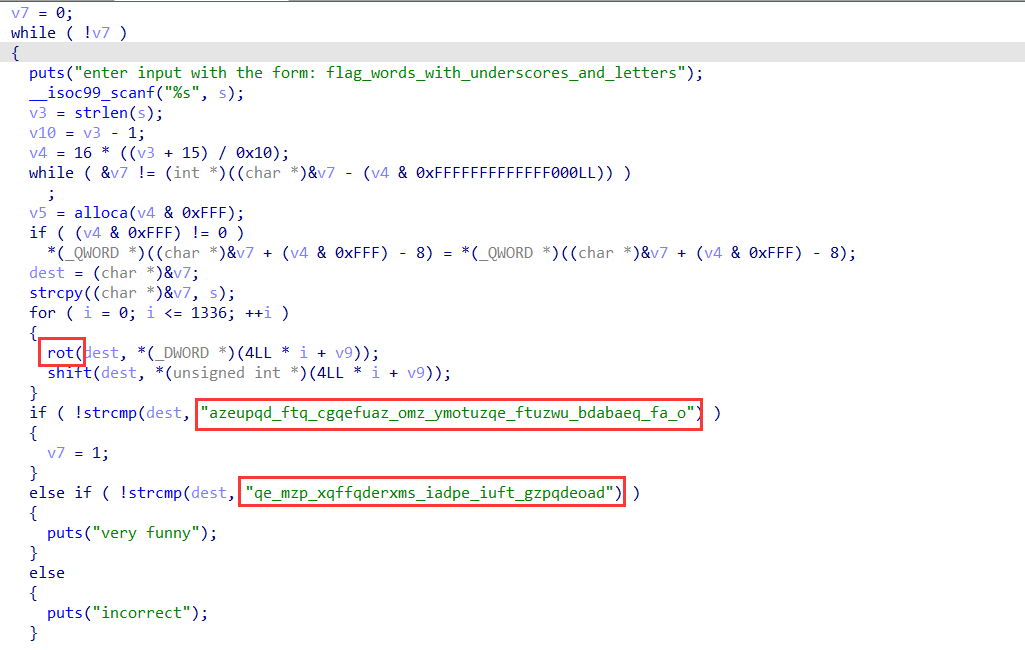
首先看到最显眼的两串字符,词频一下可以出来有含义的字符,然后发现是rot和位移,直接手撕了,输入i_propose_to_consider_the_question_can_machines_think就可以得到flag
Crypto-dhke_intro
题目提示
Small numbers are bad in cryptography. This is why.
1 | import random |
看提示是要Diffie–Hellman密钥交换,但都可以爆破,注意下hex编码
1 | # !/usr/bin/env python |
Crypto-back_to_basics
1 | from Crypto.Util.number import long_to_bytes, bytes_to_long |
当然还有一个flag_enc文件
挺有意思的题目,就是2~36进制的转换,关键函数
1 | def base_n_decode(bytes_in, base): |
Python的int真好用
手撕的,因为有些比如key的最后一位是W进制,但是U和V也没在密文里出现
Crypto-dhke_adventure
又是jo厨师傅出的题,很明显的离散对数系统的密码题,因为hint有smoother,可以想到是解离散对数的光滑数问题
1 | from random import randint |
已知
$dio=g^a\ mod\ p$
$jotaro=g^b\ mod\ p$
$key=dio^b\ mod\ p$
解题的关键是p可以由攻击者提供的,那直接提供一个光滑数+1好了,这样这个DLP离散对数求解的难题就变得可计算了,具体的推导参考pohlig-hellman攻击原理,有能力可以复现
这里直接上脚本了,首先生成一个光滑数
1 | from Crypto.Util.number import * |
直接手动接收,然后在sgae里求a和b
1 | #!/usr/bin/env python |
Crypto CTF
Farm
1 | #!/usr/bin/env sage |
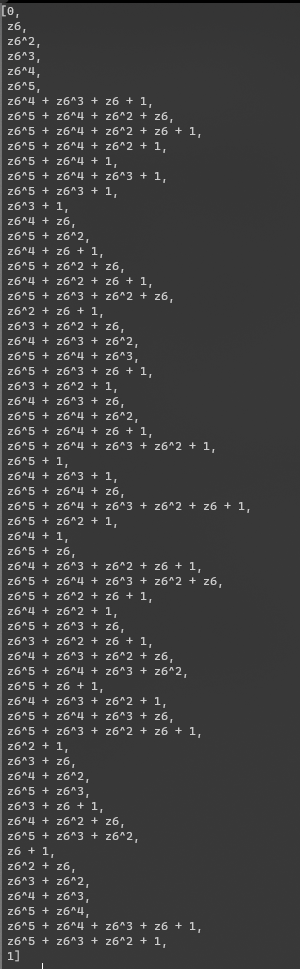
就是类似字典key和value的关系,关键的key爆破下就好了。贴下脚本
1 | import string |
然后在64个结果中找flag
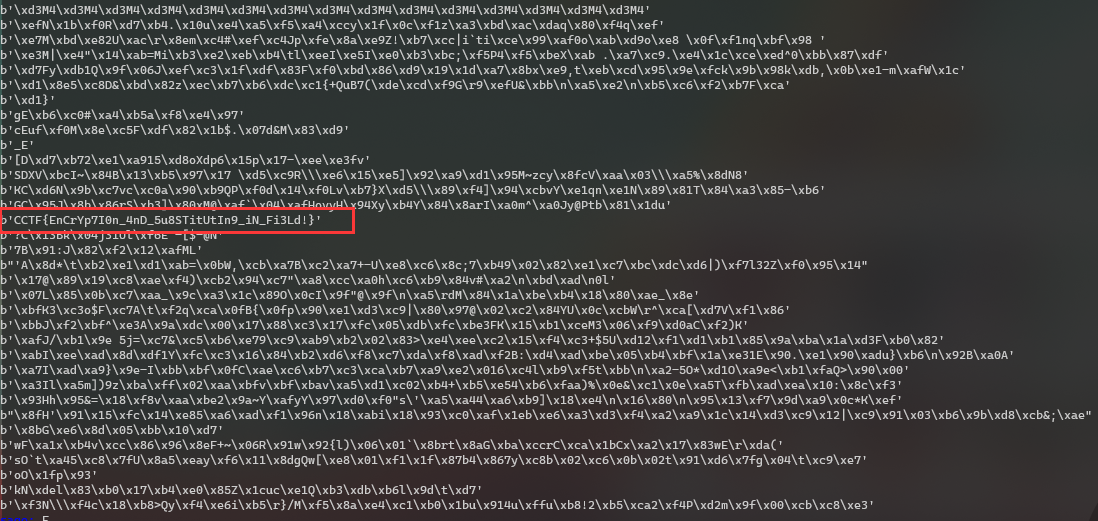
1 | CCTF{EnCrYp7I0n_4nD_5u8STitUtIn9_iN_Fi3Ld!} |
